1.4. Open Authentication (OAuth)
OAuth is an emerging authentication standard that allows consumers
to share their private resources (e.g., photos, videos, contact lists,
bank accounts) stored on one CSP with another CSP without having to
disclose the authentication information (e.g., username and password).
OAuth is an open protocol and it was created with the goal of enabling
authorization via a secure application programming
interface (API)—a simple and standard method for desktop, mobile, and
web applications. For application developers, OAuth is a method for
publishing and interacting with protected data. For CSPs, OAuth
provides a way for users to access their data hosted by another
provider while protecting their account credentials.
Within an enterprise, OAuth may play a role to enable SSO with a trusted service provider by employing a web
services SSO model. OAuth facilitates authorization of a pair of
services to interact without requiring an explicit federation
architecture. Much like OpenID, OAuth started in the consumer-centric
world to help consumer services access customer data hosted across
providers. Recently, Google released a hybrid version of an OpenID and
OAuth protocol that combines the authorization and authentication flow
in fewer steps to enhance usability. Google’s GData API recently announced support for OAuth.
(GData also supports SAML for browser SSO.)
Figure 4 illustrates the sequence of
interactions between customer or partner web application, Google
services, and end user:
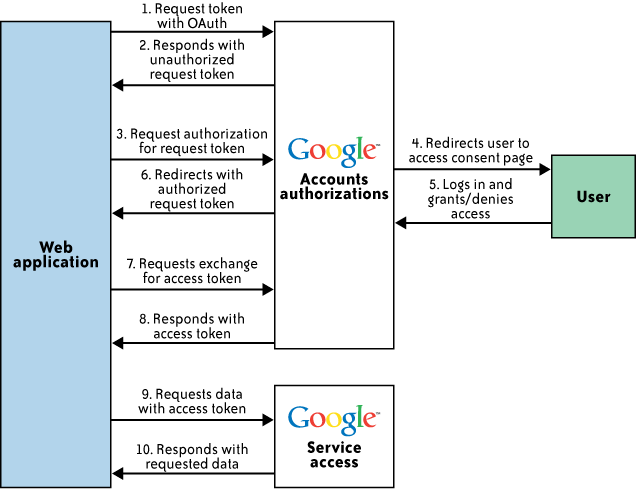
Customer web application contacts the Google Authorization
service, asking for a request token for one or more Google
service.
Google verifies that the web application is registered and
responds with an unauthorized request token.
The web application directs the end user to a Google
authorization page, referencing the request token.
On the Google authorization page, the user is prompted to
log into his account (for verification) and then either grant or
deny limited access to his Google service data by the web
application.
The user decides whether to grant or deny access to the web
application. If the user denies access, he is directed to a Google
page and not back to the web application.
If the user grants access, the Authorization service
redirects him back to a page designated with the web application
that was registered with Google. The redirect includes the
now-authorized request token.
The web application sends a request to the Google
Authorization service to exchange the authorized request token for
an access token.
Google verifies the request and returns a valid access
token.
The web application sends a request to the Google service in
question. The request is signed and includes the access
token.
If the Google service recognizes the token, it supplies the
requested data.
2. IAM Standards, Protocols, and Specifications for
Consumers
The following protocols and specifications are oriented toward
consumer cloud services, and are not relevant from an enterprise cloud
computing standpoint.
2.1. OpenID
OpenID is an open, decentralized standard for user authentication and access control, allowing users to log
on to many services with the same digital identity—i.e., a single
sign-on user experience with services supporting OpenID. As such, it
replaces the common logon process that uses a logon username and
password, by allowing a user to log on once and gain access to the
resources of multiple software systems. OpenID is primarily targeted
for consumer services offered by Internet companies including
Google, eBay, Yahoo!, Microsoft, AOL, BBC, PayPal, and
so on. OpenID adoption for enterprise use (e.g., non-consumer use) is
almost non-existent due to trust issues; some researchers have
revealed that OpenID could accelerate phishing attacks that can result in compromising user
credentials.
2.2. Information cards
Information cards are another open standard for identity on the Web. The
standard itself is directed by the Information Card Foundation, whose
steering members include representatives from Google, Microsoft,
PayPal, Oracle Novell, and Equifax. The Foundations states that its
mission is “to reduce the instance of identity theft by securing
digital identities in place of traditional logons and passwords.” The
goal of this standard is to provide users with a safe, consistent,
phishing-resistant user interface that doesn’t require a
username and password. People can use an information card digital
identity across multiple sites for convenience without compromising
their login information (similar to using an OpenID identity across
multiple sites). The Information Cards Protocol is designed for use in
high-value scenarios, such as banking, where phishing resistance and
support for secure authentication mechanisms such as smart cards are
critical business requirements.
Any service provider can implement, issue, or accept information
cards (also called i-cards). Information cards are composed using WS-*
specifications instead of HTTP redirect, so the specifications are
significantly more complicated than OpenID. Even though this system
offers great protection against identity theft and phishing, it still
has a few issues that prevent it from achieving its mission. The
greatest problem with the system is that it only works if the website
used by the consumer is participating and accepts information cards.
If this affiliation is not present, the information card is useless.
As more and more websites accept information cards, the system will
become more and more useful, but until that time, they have limited
use. For example, one can use a managed information card issued by
Microsoft Windows Live ID to provide single sign-on to most of
Microsoft’s sites, including MSDN, TechNet, Live, and Connect.
2.3. Open Authentication (OATH)
OATH is a collaborative effort of IT industry leaders aimed at
providing an architecture reference for universal, strong
authentication across all users and all devices over all networks. The
goal of this initiative is to address the three major authentication methods:
Subscriber Identity Module (SIM)-based authentication (using a Global System for
Mobile Communications/General Packet Radio Service [GSM/GPRS]
SIM)
Public Key Infrastructure (PKI)-based authentication (using an X.509v3
certificate)
One-Time Password (OTP)-based authentication
This authentication protocol leverages well-established
infrastructure components, such as a directory server and a Remote
Authentication Dial-In User Service (RADIUS) server, and also leverages federated identity
protocols.
2.4. Open Authentication API (OpenAuth)
OpenAuth is an AOL-proprietary API that enables third-party websites and applications
to authenticate AOL and AOL Instant Messenger (AIM) users through
their websites and applications. Using this authentication method, an
AIM- or AOL-registered user can log on to a third-party website or
application and access AOL services or new services built on top of
AOL services. According to AOL, the OpenAuth API provides the
following features:
A secure method to sign in. User credentials are never
exposed to the websites or applications the user signs
into.
A secure method to control which sites are allowed to read
private or protected content.
Automatic granting of permissions only if the user selects
Allow Always on the Consent page.
A prompt for user consent when the website or application
attempts to read any private or protected content (e.g., separate
consent requests to allow Buddy List information, to send IMs, to
read albums).
Access to other non-AOL websites without the need to create
a new user account at each site that supports AOL OpenAuth
APIs.
Given the proprietary nature of the protocol, the cloud
computing community does not regard OpenAuth as an open standard, and
OpenAuth is not adopted outside the AOL network.
3. Comparison of Enterprise and Consumer Authentication Standards
and Protocols
Given that various “Open*” acronyms are being circulated in the
context of authentication, authorization, and federation protocols and
standards, Table 1 is
an attempt to compare them from the point of open standards support and
their relevance in enterprise and consumer cloud services.
Table 1. Comparison of IAM standards and protocols
| IAM protocols and
standards | Enabling
vendors | Enterprise cloud
customer requirements | CSP
requirements |
|---|
| SAML | IdM software vendors such as Sun, Oracle, CA, IBM, and Novell, and identity
management service providers such as Microsoft Azure, Symplified, TriCipher, and Ping Identity | Support strong
authentication and web SSO, avoid duplication of identity, and
share only selected attributes to protect user
privacy | Enable customers to
delegate authentication and choose authentication methods (e.g.,
dual-factor authentication using corporate identity) that enable
adoption of the cloud service |
| XACML | Supported by Sun, CA, IBM, Jericho Systems, Oracle, Red Hat,
Securent (Cisco), and Oracle | A standard way to express
authorization policies across a diverse set of cloud services
and externalize authorization and enforcement from the
application | Support authorization
that can represent complex policies required by enterprise-scale
applications and administrators |
| OAuth | Supported via an API by service providers including Google,
Twitter, Facebook, and Plaxo | Publish and interact with
protected data stored on one CSP and accessed from another CSP
using a standard API and without disclosing
credentials | Enable users to access
their data hosted by another service provider while protecting
their account and credential information |
| OpenID | Supported by many service providers including Google, IBM, Microsoft, Yahoo!, Orange, PayPal,
VeriSign, Yandex, AOL, and USTREAM | Not adopted due to trust
issues | Support SSO for consumers
participating in this federated identity service |
| OATH | Supported by many authentication hardware and software
vendors including VeriSign, SanDisk, Gemalto, and
Entrust | Not
relevant | Not
relevant |
| OpenAuth | Supported by AOL only for users accessing partner
services | Not
relevant | Support AOL users
accessing partner applications using AOL or AIM user
IDs |